Zoom Beefs Up User Security With End-To-End Encryption
5 min read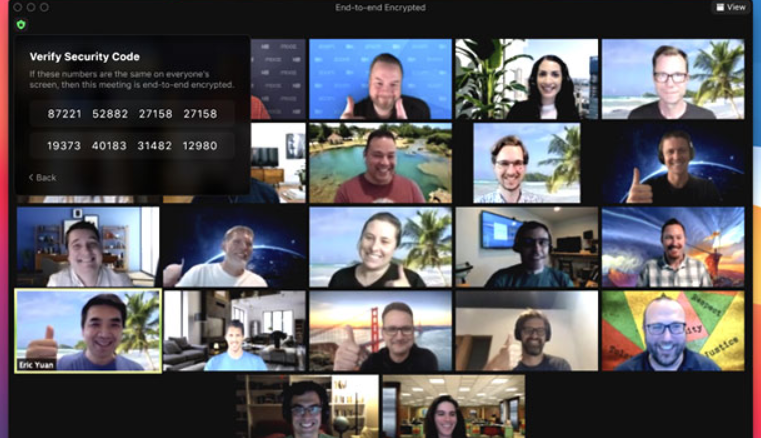
Zoom offered its individuals a large protection upgrade Monday when it turned out end-to-end file encryption for its on-line conferences network.
E2EE places control of the secrets for clambering information in the hands of conference coordinators. Prior to the E2EE rollout, file encryption was done on Zoom’s web servers, where a person with accessibility to those web servers can obstruct the information.
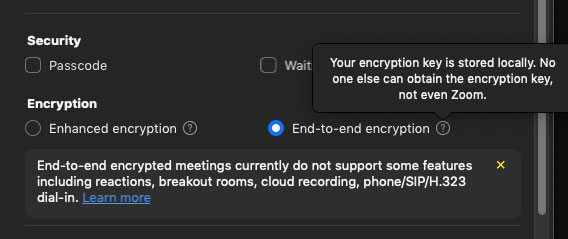
To utilize the brand-new attribute, consumers have to allow E2EE conferences at the account degree as well as opt-in to E2EE on a per-meeting basis.
“Distributing tricks to the customers and also decentralizing count on provides customers raised guarantee that their interactions are much less most likely to be obstructed via jeopardized tricks or framework,” Jack Mannino, CEO of nVisium, an applications protection carrier in Herndon, Va., informed TechNewsWorld
Without end-to-end security, there’s an opportunity that somebody with accessibility to the system might obstruct discussions, clarified Dan Nadir, primary item policeman at Theta Lake, a safety as well as conformity services carrier for partnership systems in Santa Barbara, Calif.
“That might be an underhanded worker, or somebody that has the ability to breach the system,” he informed TechNewsWorld. “Full end-to-end file encryption removes this possible factor of susceptability.”
Unconcerned Servers
In common conferences, Zoom clarified in a declaration, its cloud conference web servers creates file encryption secrets for each conference as well as disperses them to conference individuals utilizing Zoom customers as they sign up with.
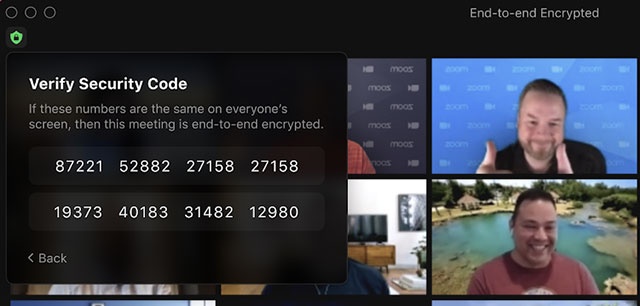
With Zoom’s brand-new E2EE, it proceeded, the conference’s host creates file encryption secrets and also utilizes public essential cryptography to disperse these secrets to the various other conference individuals, that will certainly additionally see the conference leader’s protection code that they can utilize to validate the safe and secure link. The host can review this code aloud, and also all individuals can examine that their customers present the very same code.
Zoom’s web servers come to be unaware relays as well as never ever see the file encryption tricks called for to decrypt the conference materials, it clarified. Encrypted information passed on via Zoom’s web servers is illegible by Zoom, because Zoom’s web servers do not have the required decryption secret.
“We’re extremely pleased to bring Zoom’s brand-new end-to-end security to Zoom individuals around the world today,” Zoom CISO Jason Lee claimed in a declaration.
“This has actually been an extremely asked for attribute from our consumers, and also we’re delighted to make this a fact,” he included.
Restraining Zoom Bombing
When utilized appropriately, E2EE can make it challenging for also the best-resourced knowledge firms on the planet to be all ears on interaction utilizing it, observed Tod Beardsley, supervisor of study at Rapid 7, an information and also analytics safety remedies company in Boston.
“That’s why it’s such an effective system for making sure personal privacy for the sort of individuals that require to bother with knowledge companies– reporters that are safeguarding resources, whistleblowers, civil liberties protestors, and also others,” he informed TechNewsWorld.
“The advantage for customers, specifically in COVID times, is considerable,” included Dirk Schrader, international vice head of state of New Net Technologies, a Naples, Fla.-based company of IT safety and security and also conformity software application.
“That’s specifically real free of cost individuals,” he informed TechNewsWorld. “Around the world numerous institutions as well as volunteer companies have actually been making use of Zoom to interact, amidst issues regarding personal privacy as well as safety.”
Among the very early issues encountered by individuals of the system was “Zoom Bombing,” where burglars got into conferences and also interrupted them. “E2EE can quit that,” kept in mind Chris Carter, CEO of Approyo, an SAP companies in Muskego, Wis.
“No one can go into a meeting prior to the host,” he informed TechNewsWorld. “Anyone getting in an E2EE meeting needs to supply info regarding themselves, as well as the host needs to accept them. They can not go into as a confidential visitor.”

Concern About Crime Carter included that there were tradeoffs for making use of Zoom’s E2EE function. “If you have E2EE on, you can not tape-record conferences to Zoom’s web servers,” he described. “You can not do personal conversations or outbreak spaces.”
Although E2EE is being supplied to both complimentary and also paying customers of Zoom, the firm at first recommended restricting the function to paying individuals over worries the modern technology could be abused by wrongdoers. That capacity still exists.
“As system solutions transfer to end-to-end security, it suggests that there is much less chance for company and also police to spot wrongdoers as well as individuals making use of a solution for destructive functions,” claimed William Dixon, head of cybersecurity for the World Economic Forum, a worldwide company for public-private collaboration, headquartered in Geneva, Switzerland.
What that indicates, he proceeded, is individuals are needing to introduce and also progress their reasoning on discovering criminal activity on these systems. “Technology companies have actually been utilizing a range of strategies to discover destructive task,” he informed TechNewsWorld. “They’re spending greatly in evaluation at the metadata degree and also of customer analytics to give suggestions to police of possible questionable task.”
While including E2EE is an advantage for Zoom individuals, the business is additionally gaining from the step. “It brings them as much as a degree of safety that a Microsoft normally has,” Carter kept.
“Basically Zoom had no option,” claimed Schrader. “Adding E2EE file encryption to its solutions was a should besides the chaos it experienced.”
Low point insisted that end-to-end file encryption is table risks for any type of firm that wishes to give a severe service for basically any kind of usage instance.
“Since it is table risks for interactions systems, not having it is certainly an affordable drawback for any type of modern technology in the industry,” he included.
Solitary Sign-on On Horizon
The brand-new security function is readily available to both cost-free and also paid customers as well as on Mac as well as computer desktop computer variation 5.4.0 of Zoom, along with the Android version of the application and also Zoom Rooms.
It makes use of the exact same 256-bit AES-GCM file encryption made use of to safeguard non-E2EE conferences.
Zoom is calling this preliminary rollout of E2EE a “technological sneak peek.” it wants to collect input from clients on their experiences with the function and also motivates clients to make it possible for Feedback to Zoom on their accounts as well as utilize it to discuss the brand-new attribute.
Zoom kept in mind that this is simply the starting stage of E2EE for it. The following stage will certainly consist of far better identification administration and also solitary sign-on.
“Identity monitoring and also solitary sign-on assistance will certainly make it simpler for venture clients to make use of Zoom as a partnership system. It will certainly minimize rubbing for end customers,” Jeff Pollard, a vice head of state and also major expert at Forrester Research, informed TechNewsWorld
“This performance boosts and also finishes E2EE,” included Schrader.
“By mistreating a taken identification, an assaulter can sign up with an encrypted session posing the genuine identification to collect real-time details,” he clarified. “These techniques are not distinct to Zoom, they prevail for all sort of solutions.”